INDUSTRY
telecommunications
Securing Australia’s Telecommunications Sector
Why CyberLock’s electro-mechanical master key system is the best solution for securing our telecommunications industry.
[1] https://www.homeaffairs.gov.au/nat-security/Pages/telecommunications-sector-security-reforms.aspx
The telecommunication industry is as significant as it is challenged. It allows us to communicate and stay in touch with friends and loved ones and more importantly it’s the bridge between emergency responders and civilians in times of emergency or as Home Affairs describes “vital to the delivery and support of other critical infrastructure and services such as power, water and health”[1]. So, protecting our telecommunication assets should be top of mind, not just for our telecom security managers but you and I as well.
Due to the unique nature of their organisational structure, telecom companies face a number of security challenges. Frequently, telecom utilities are geographically widespread, sometimes even spanning across states. Many of these assets are also remote, isolated infrastructure sites without onsite staff which makes them increasingly vulnerable to thieves, vandals and arson attacks.
A recent example of such vandalism was in March of 2022, when a Telstra 5G tower was set alight causing a wide spread service blackout for the town of Mullumbimby and beyond[1]. A town in which was in midst of a flood crisis and communication with emergency responders was crucial.
It’s examples like the above that in 2018 the Telecommunications Sector Security Reforms (TSSR) made amendments to the Telecommunications Act 1997 to btter manage the national security risks associated with the telecommunication sector. All carriers, carriage service providers and carriage service intermediaries will be required to do their best to protect networks and facilities from unauthorised access and interference — including a requirement to maintain ‘competent supervision’ and ‘effective control’ over telecommunications networks and facilities owned or operated by them[2].
Moreover, to effectively secure and control this vast network of resources, telecom companies have little choice but to rely on a complex web of dynamic work orders and rotating personnel or contractors. Managing who has access rights, and perhaps more importantly, when they exercise those rights is essential to maintaining secure operations. And as telecommunication technology advances, personnel require access to a rapidly evolving labyrinth of equipment, from remote towers to densely deployed rooftop antennas.
Telecommunication towers
Telecommunication towers transmit a number of communication signals that we use all day, everyday. Mobile phone services, radio and TV broadcasting, GPS and emergency medical services are several examples of industries that rely on these towers to function. If there is an issue with a tower, or its security has been breached it can wreak havoc on a region on more than one front which is why securing them is vital. As mentioned above, due to an arson attack, the town of Mullumbimby recently lost all communication connection. There have also been several other attacks on 5G towers across the country in light of the recent pandemic[1].
[1] https://www.theguardian.com/technology/2020/may/27/5g-fires-australian-mobile-companies-work-with-police-to-prevent-arson-attacks
Telecommunication huts
Telecommunication huts or shelters house and protect a range of highly sensitive communication equipment. From data storage, generators, fibre optic cables and more these huts are typically made to withstand the elements and if breached could cause great distress to the network. Often, these huts are also geographically spread out and require a security system that is both accessible by many and sturdy enough to also withstand not only its environment but any malicious attacks or threats.
Why choose CyberLock for your telecom facility?
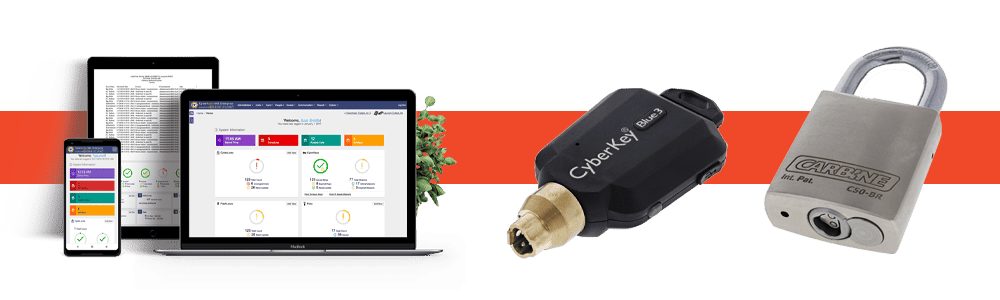
EKA CyberLock is a fully electronic electro-mechanical master key system that combines the best features of electronic and mechanical master key systems. Utilising CyberLock smart CyberKeys and CyberLock communicators to power CyberLock cylinders and locks, no hardwiring or cabling is necessary which makes CyberLock an ideal solution for telecommunication utilities.
CyberKeys can be scheduled to open specific locks for a specific amount of time making them perfect for one-time users such as contractors and if ever a CyberKey is lost it can simply be removed from the system rendering it useless which means there is not threat of key copying or manipulation.
CyberLock cylinders retrofit into most applications including padlocks which means securing remote assets like telecommunication shelters or towers is easy. No cabling or networking needed, as a CyberLock is powered when inserted with a CyberKey.
CyberLock cylinders are also IP68 rated meaning they do not need a weather protector and are the perfect weather and element resistant option being water proof, dust proof and operational in temperatures as low as -40 degrees and as high as 70 degrees.
BAI Communications are one of the latest telecom companies to install EKA CyberLock. This two-staged security upgrade has seen BAI enhance their site access capability with CyberLock and are now better equipped to control who accesses their sites when using CyberKeys and CyberLocks. It has simplified their key management processes and allowed BAI to configure one key to access all sites and zones, including their towers and huts, for their contractors so they are only able to access locks at predetermined times.
So far, stage one has seen BAI issue 1661 CyberKeys and install 1745 CyberLocks across 395 sites including telecom towers, huts and gates. They have centralised and automated their access capabilities. Stage two is currently underway and will include integrating BAI’s CyberLock system with their existing security programs and software so as to streamline their processes and have one place to access all security information.
For more information on our BAI Communications case study, please click below.
SYDNEY • MELBOURNE • BRISBANE • PERTH • ADELAIDE • AUCKLAND




