COMMUNICATION
devices
Communicators underpin the flexibility of EKA CyberLock.
Simple, instant key activation.
Communicators serve as the interface between CyberKeys and the CyberAudit management software.
Through a communicator, CyberKey information is downloaded into the software and new schedules and permissions are updated on the CyberKeys.
A variety of communicators are available to address individual facility and personnel needs. Communicators can be installed in locations that are easily accessible to your CyberKey holders such as an employee entrance, sign in desk or even a car park access point, making frequent CyberKey expirations and access programming convenient for higher security.
A network of communicators allows users to validate their CyberKeys without returning to where the EKA CyberLock software is hosted, instantly downloading audit trail data and receiving updated access permissions. Some communicators are also designed to recharge rechargeable CyberKeys.
This network can also extend to mobile communicators such as the CyberAudit Link app, giving users the flexibility to update keys in the field via Bluetooth, without relying solely on fixed locations.
Communicators are so versatile that they can be mounted almost anywhere, maximising ability to control access to even the most remote assets.
facts
Functions
Updates
Key Type
Availability
validikey pro 2
Ideal for large facilities, this intelligent key cabinet stores keys in an inactive state.
An RFID card or PIN code is required to activate a CyberKey and when a
CyberKey is returned to the vault, it automatically deactivates with a full audit of the CyberKey activities uploaded to CyberAudit Web
authoriser keypad
A durable, weather-proof unit that is fitted to the exterior of a building or facility.
Users present their key to the authoriser and enter a PIN code to obtain permission privileges.
validikey 2 vault
This vault can hold and program up to two CyberKey smart keys. It has a door that locks to secure the keys until an approved RFID card is scanned or a mission number is entered on its display keypad.
After verifying the mission from its internal cache, the ValidiKey 2 programs a key with that user’s permissions, unlocks the door and prompts the user to remove the key.
usb station
In a smaller office, when your CyberAudit might only sit on a desktop, a simple USB station port is a cost-effective way to authorise keys.
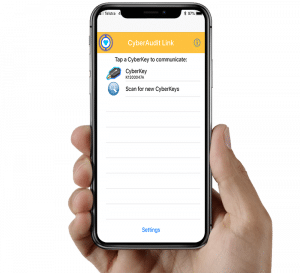
cyberaudit link app
The smart device app enables each user to activate & deactivate a CyberKey Blue 2 in-situ, as well as communicate with CyberAudit, allowing real time audit reporting and update of permissions.
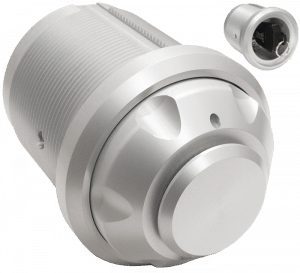
cyberkey vault
The CyberKey Vault houses a single CyberKey. The unit is an extremely secure, rugged, outdoor vault that stores an un-programmed CyberKey.
When approved credentials are presented, the CyberKey is programmed and can then be removed from the vault.